
Defensys tip
Automated collection, processing and monitoring of IOCs
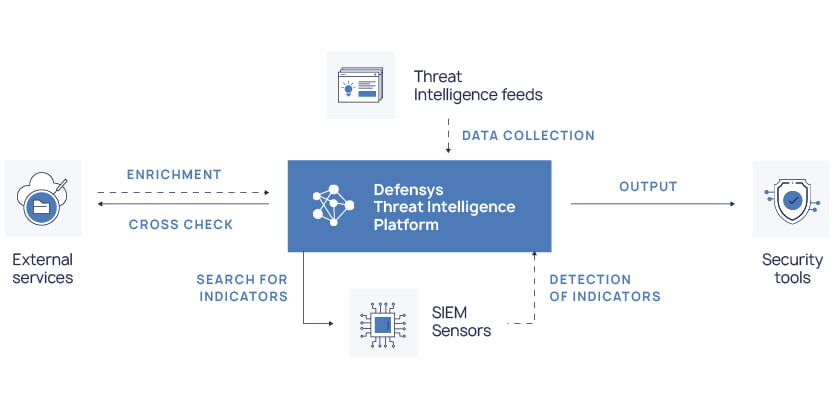
Defensys Threat Intelligence Platform facilitates comprehensive management and use of threat intelligence and also enables centralized collection and prioritization of indicators of compromise, enriched with additional context and direct output of ready-to-use data to security controls and systems.
Defensys tip
Benefits
- Facilitates TI management through the centralized collection, normalization, prioritization and storage of threat intelligence data from multiple sources.
- Accelerates incident investigation by means of additional enquiries, instant search across all available TI feeds and automated workflows.
- Helps to reveal hidden threats via automated monitoring of SIEM using sensors.
- Allows immediate threat blocking and minimization of possible damages by leveraging direct output of data to internal security systems.
Key Features
Collection & Processing
Defensys Threat Intelligence Platform collects threat data from multiple sources and performs their automated processing and prioritization. The software performs normalization and de-duplication of data across feeds and serves as a central repository for all threat data, eliminating manual and repetitive work.
Defensys TIP automatically aggregates threat intelligence data from multiple sources. The system has built-in integration with threat intelligence data exchange websites and services, such as:
- Own Defensys Feed
- IBM X-Force Exchange
- AT&T Alien Labs Open Threat Exchange (OTX)
- Group-IB Threat Intelligence
- Kaspersky Threat Intelligence
- ESET Threat Intelligence
- RST Cloud Threat Feed
- Defensys collection of useful open source feeds
- And other sources
Context & Enrichment
Defensys TIP enriches data with additional context and performs additional checks and queries in the external services. More complete, detailed and accurate intelligence improves situational awareness and helps the analyst to better decide upon incident response and to take timely actions.
Enrichment services supported:
- VirusTotal
- Hybrid Analysis
- OPSWAT Metadefender
- Shodan
- RiskIQ
- MaxMind
- Sypex
- Ipgeolocation.io
- Whois
Correlation & Analysis
Defensys TIP collects and correlates additional information associated with an IOC, including:
- Reports on tactics, techniques and procedures (TTPs) of threat actors
- Malware
- Vulnerabilities used
- Other associated IOCs
The analysis of the relationships facilitates the correct interpretation of data allowing the analyst to understand the adversary and get the whole picture of the threat.
Delivery & Response
Ready-to-use data is automatically delivered to internal security controls and systems ensuring immediate response and reducing false positives.
Monitoring & Detection
Defensys TIP ensures real-time monitoring and detection of relevant IOCs in the infrastructure and immediately notifies the security analyst in case of detection. The platform also supports retrospective searches of data in the SIEM events using sensors.
Automation
Defensys Threat Intelligence Platform automates all repetitive operations with IOCs including collection, enrichment, detection, data output and notifications eliminating manual routine tasks. It makes it possible to completely automate the whole lifecycle of an IOC, from its collection to blocking by security tools, with the help of adjustable processing rules.
