
Defensys soar
Comprehensive Security Automation, Orchestration & Response
Defensys Security Orchestration, Automation & Response (SOAR) Platform represents a comprehensive software platform for security automation and orchestration which can serve as a basis for building the internal Security Operations Center.
Defensys SOAR aggregates all security incident data from various sources in a single database for further analysis and investigation and facilitates agile incident response through automated workflows and playbooks.
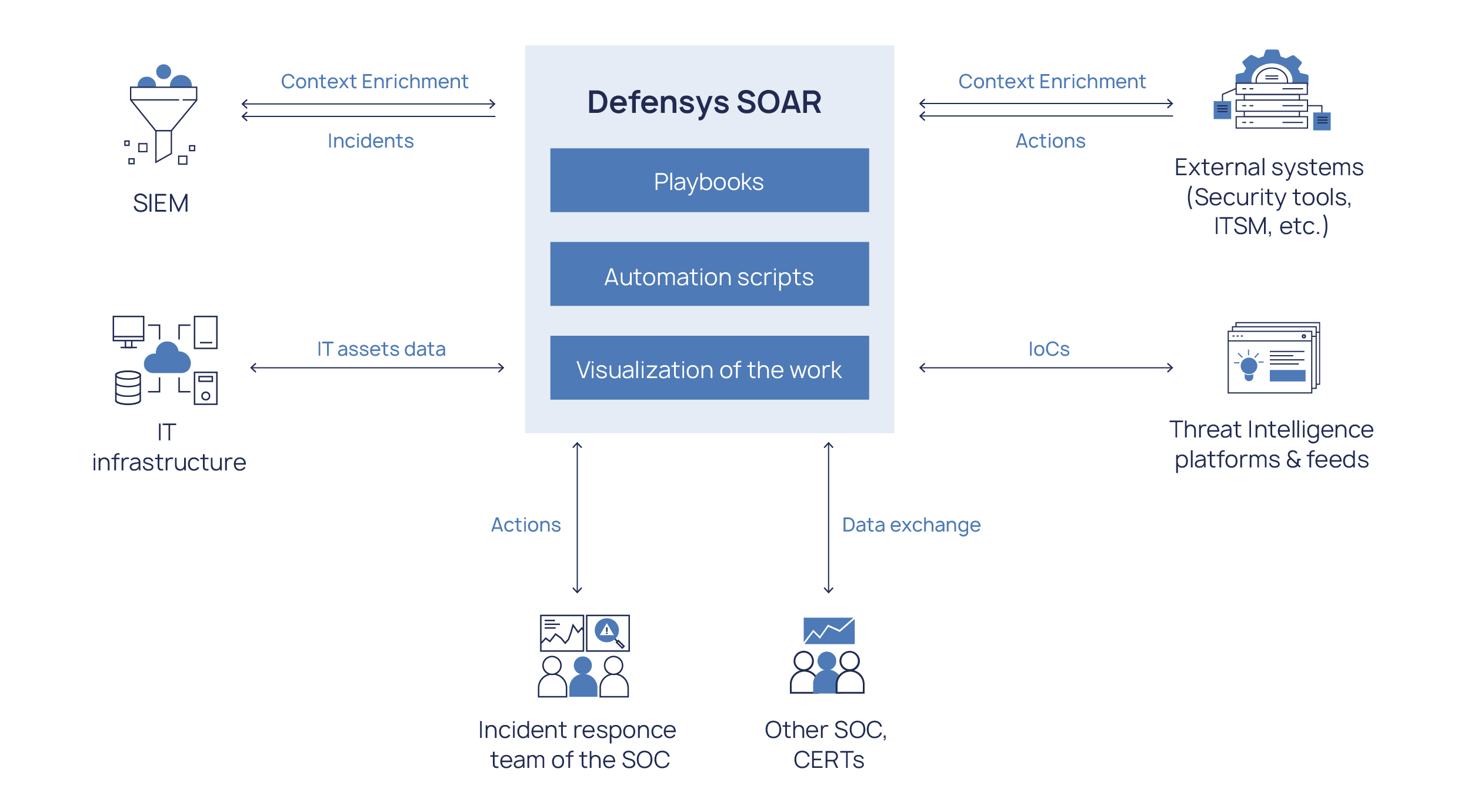
Defensys soar
Key Benefits
Key Features
Incident Response Automation
The speed of incident response is one of the key performance indicators of an information security team. With a rising number of incident alerts and outbreaks of cyberattacks, the only way to address them promptly is to automate the incident workflow and develop ready-to-use response plans.
Defensys SOAR automates most of the routine time-consuming operations streamlining incident response and allowing the security operation team to focus on advanced analytics and threat defence.
The platform offers an advanced set of automation tools including
- Dynamic playbooks;
- A set of ready-to-use scripts;
- Adjustable workflows;
- Security tools orchestration.
Dynamic Playbooks
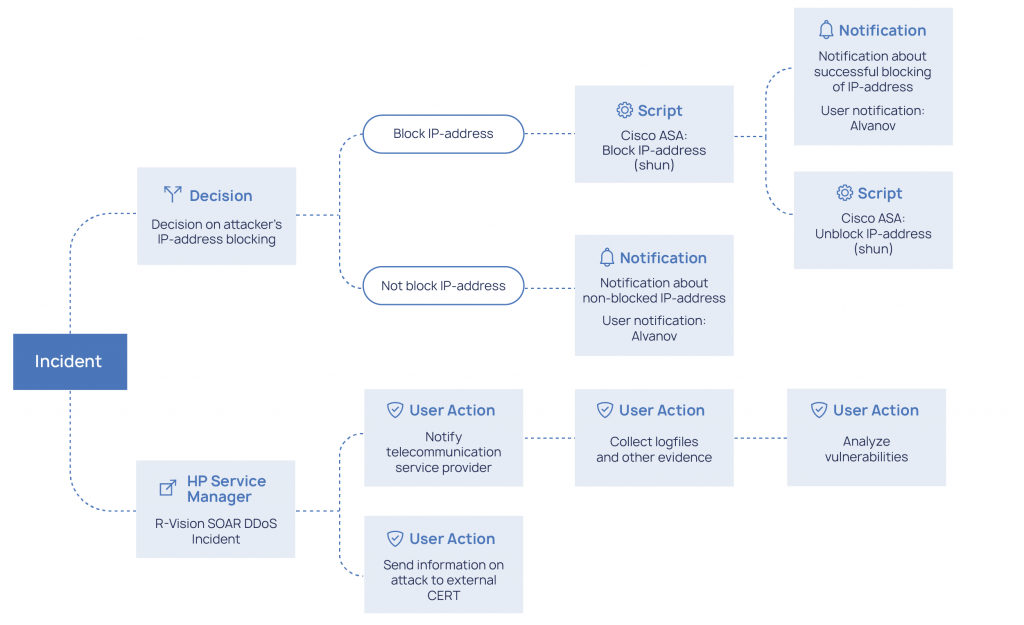
Defensys SOAR offers adjustable built-in dynamic playbooks which allow specifying a sequence of actions for the particular incident type that will be executed in case of an alert automatically. Playbooks can contain multiple action variants with automated, manual or mixed decision-making.
Typically, a playbook comprises standard actions like notification, case and task assignment, remote commands to hosts and security tools, remote data collection, etc. Each playbook can be visualized to check the consistency of the response.
SOC Team collaboration
- Centralized assignment of tasks with an option to control each team member’s role and access to data. All planned and performed security activities are displayed at one single panel.
- A common workspace for members of the SOC team working on the same case which ensures easy access to all collected evidence and data.
- Chat, commenting and other built-in communication tools streamline collaboration across teams.
IT Infrastructure Control
Defensys SOAR provides a comprehensive insight into the company’s IT infrastructure and security level by collecting data via built-in inventory tools and from integrated security solutions.
IT infrastructure control functionality allows the security teams to
- establish relationships between IT assets and business processes;
- determine critical assets;
- identify unauthorized devices;
- detect the external connections;
- control the installed software and reveal unauthorized software;
- control user privileges;
- manage vulnerabilities.
The infrastructure can be visualized on maps, floor plans and schemes with indication of incidents and vulnerabilities.
Centralized Data & Evidence Collection
Defensys SOAR captures all security-relevant data and evidence from multiple sources in a single database for further analysis, response and investigation. Original data is enriched with additional details and findings.
Centralized data and document storage facilitates easy access and information sharing among team members and improves compliance with regulatory security standards and guidelines.
Built-in integration with the e-mail server helps to engage external employees or experts to incident investigation and send them requests for information directly from Defensys SOAR console. The history of communication as well as attached documents and materials will be saved and added to the incident description.
Flexible settings
The software is fully customizable. It contains ready-to-use lists of possible actions, scripts, incident types, user roles, etc. which can be easily adapted to the company’s specific workflows and environment.
Features that maximize flexibility include
- incident description builder with an adjustable set of data to be collected for each indent type;
- graphic playbook editor which allows specifying incident management workflow of any kind;
- configurable incident templates and catalogues facilitating data input;
- flexible rule settings allow controlling access to incident data and automated assignment of the responsible personnel based on predefined criteria.
Out-of-Box Integrations
Defensys SOAR provides built-in integrations with a wide range of commonly adopted security tools and systems. Open API and universal connector via e-mail allow building custom integrations.
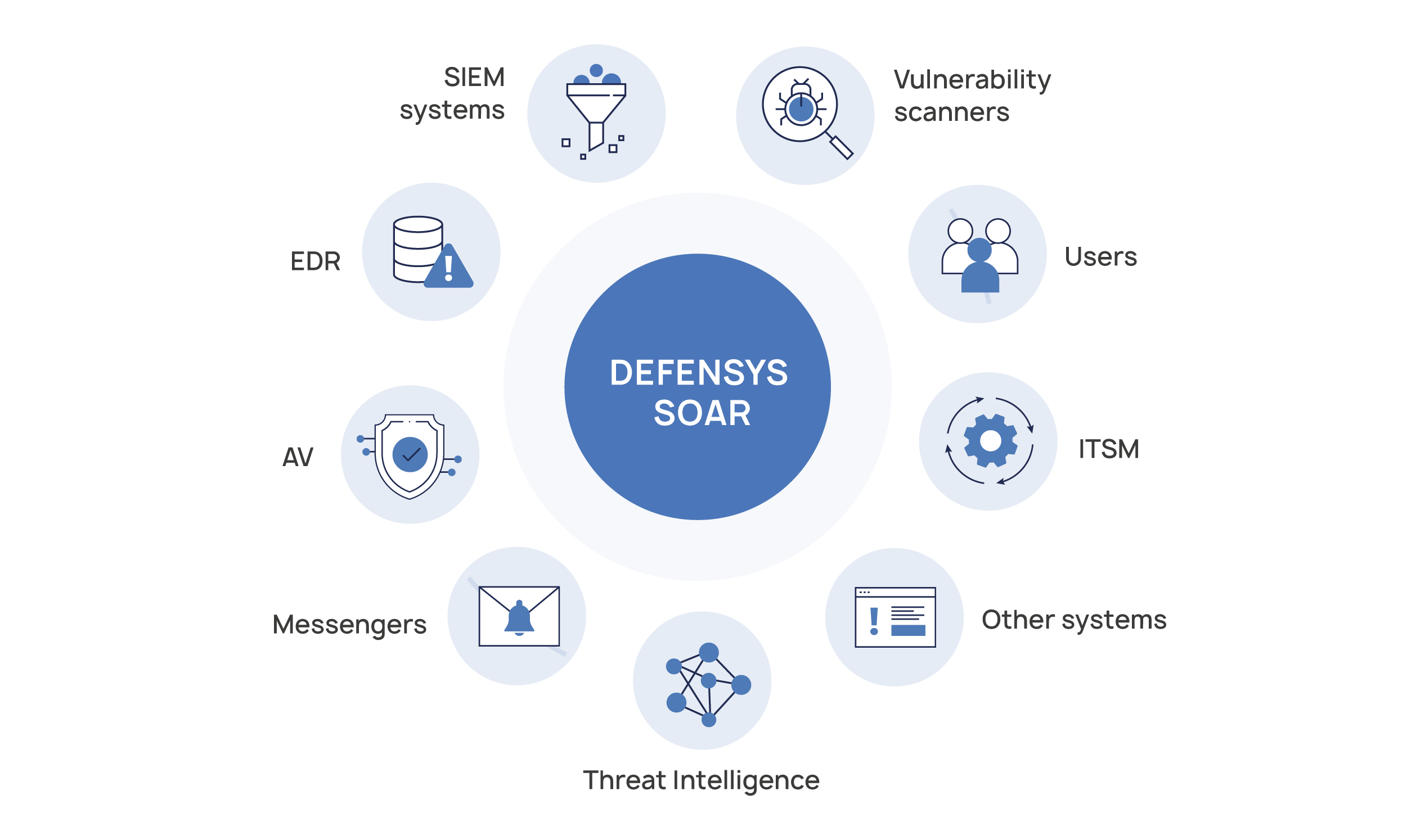
Defensys soar
Incident Data Sharing
Built-in tools for incident data sharing arrange for collaboration with trusted partners, external experts, communities and public CERTs or SOCs. Real-time data exchange gives companies access to the most actual high-quality data facilitating early threats detection and faster response.
Defensys SOAR Platform user completely controls data volume and the list of recipients during the information transfer.
Performance Tracking & Reporting
Defensys SOAR brings visibility into security operations through
- Geographical maps, network maps & floor plans with a display of assets and indication of incidents;
- Relation maps with a display of relationships between assets and systems which facilitate incident investigation;
- Automated generation of reports using predefined templates or a custom report builder and scheduled delivery to recipients;
- Incident metrics help to track performance and identify directions for improvements.
