Defensys sense
Advanced analytics for threats and anomalies detection
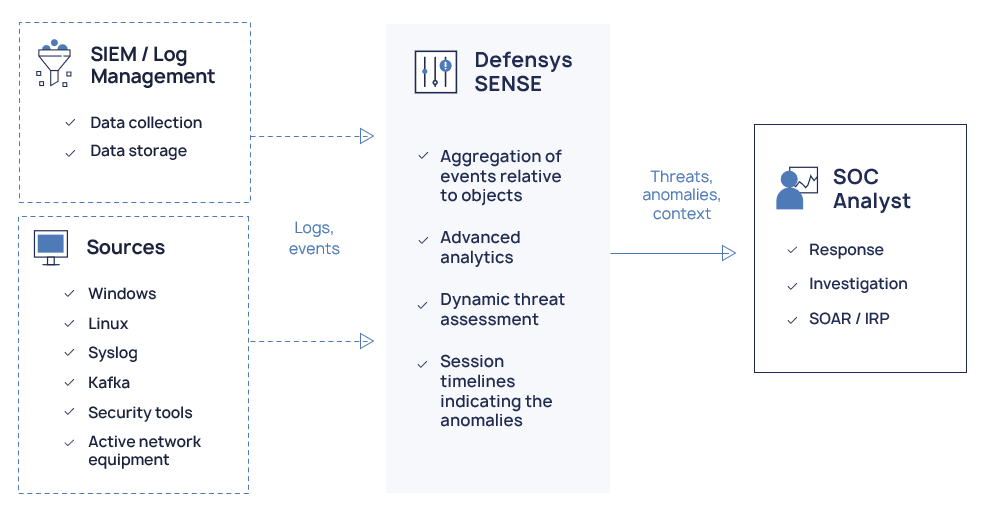
Defensys SENSE is a cybersecurity analytics platform that can detect system status violations and suspicious object activity and perform dynamic threat and anomaly assessments.
The platform has advanced analytical capabilities to improve SOC performance. In addition, it enables timely detection of incipient attack signs and prioritizes threats for response among the flow of suspicious events and incidents.
Key benefits
Key Features
Object-centric approach
Defensys SENSE performs comprehensive security event analysis using data from multiple sources, including log management systems, SIEM, and others. Security events are not analyzed individually but rather in relation to specific objects, like users, workstations, files, accounts, services, etc.
By studying object behaviour, Defensys SENSE generates normal behaviour profiles and captures suspicious activity at the slightest deviation. This object-centric approach prevents emerging threats and allows you to see deeper into potential attacks.
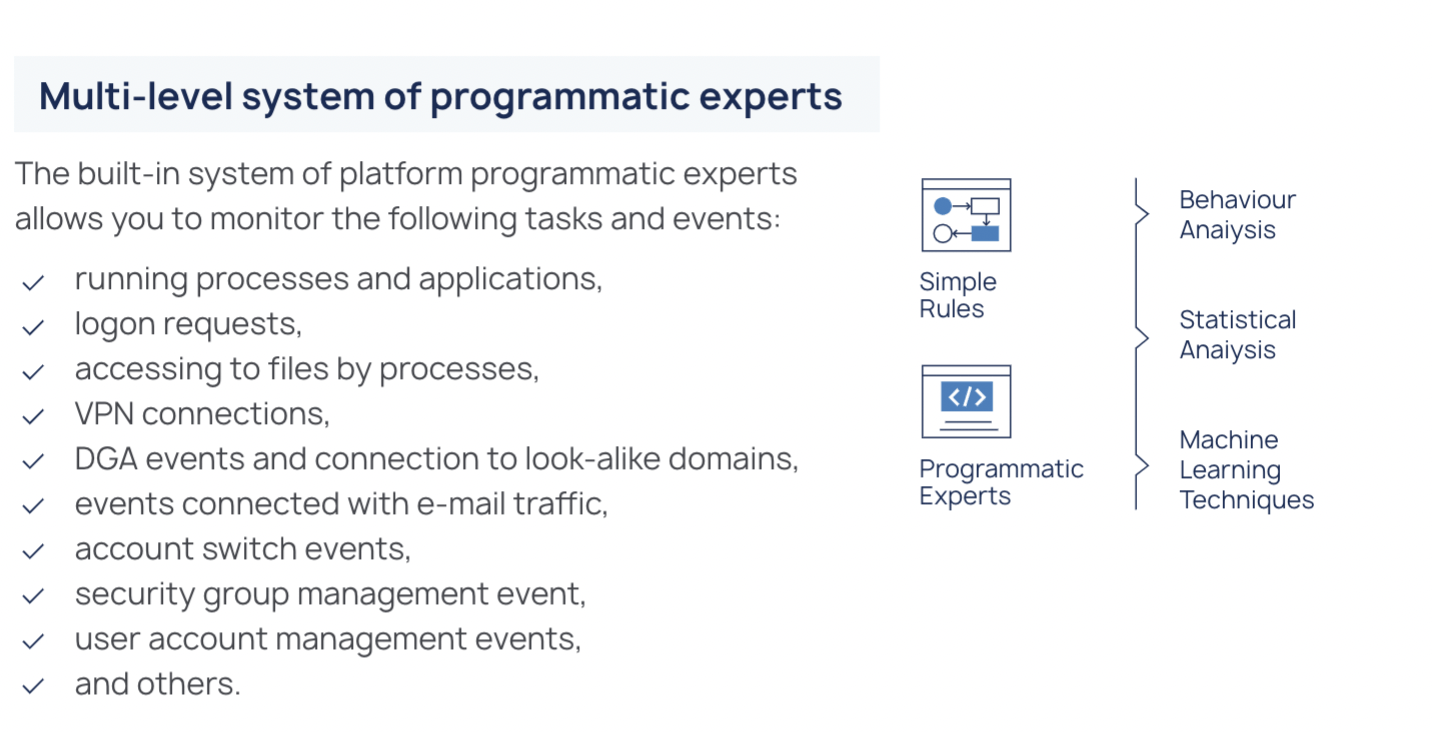
Multi-level system of programmatic experts
To detect anomalies and suspicious events, Defensys SENSE uses simple rules and a multi-level system of programmatic experts that provide:
- Logon events monitoring
- Email traffic monitoring
- Process execution monitoring
- Monitoring file access from processes
- Identifying DGA and look-a-like domains
- Detecting anomalies in VPN connections
Adaptive correlation
Defensys SENSE‘s adaptive event correlation mechanism automatically improves the integrated anomaly detection analytics. This way, as new data sources and models are added, no additional configuration of rules and programmatic experts is required, so Defensys SENSE requires minimal resources for maintenance.
Dynamic threat and anomaly assessment
The dynamic threat and anomaly assessment system calculates the severity rating of the monitored objects. If suspicious activity is detected, the object rating increases, and in case an acceptable level is exceeded, Defensys SENSE will notify the analyst about the threat. Dashboards allow monitoring changes in ratings for all objects in real time.
Dynamic assessment helps to timely notice significant anomalies in the security state and prioritize threats for a response.
Event Timeline
Detailed information about suspicious object activity is saved in the form of a timeline – a chronological sequence of events where anomalies are marked. The timeline makes it much easier to analyze incidents and identify security problems for treatment.