
Defensys Security GRC Platform
Cybersecurity control, risk management and compliance automation
Defensys Security GRC Platform (SGRC) is a comprehensive software for information security automation, IT infrastructure control, cyber security risk and compliance management.
Defensys SGRC allows calculating risks by using one of the built-in methodologies and keeping eye on risk level changes, producing a risk mitigation action plan and controlling its implementation status.
The software enables automated security audits and checks for compliance with industry security standards and best practices. In addition to ISO 27001, PCI DSS v.3.2, SWIFT and NIST which are available out-of-box, Defensys SGRC supports the import of proprietary standards, risk methodologies and threat databases.
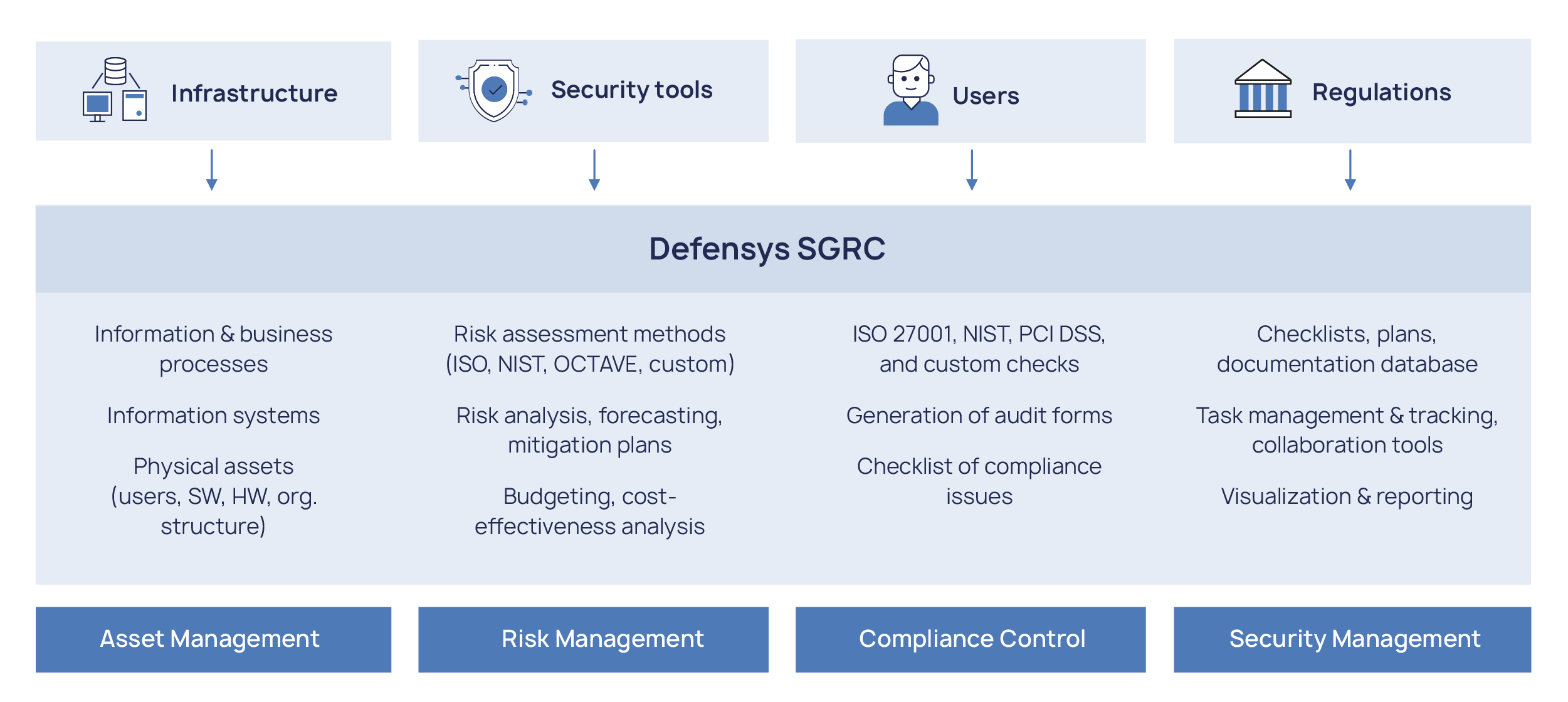
Defensys sgrc
Key Benefits
Information Security Management
Defensys SGRC Platform collects and stores data about information security processes and enables its visualization facilitating decision making, prioritization of required measures and budgeting.
Built-in metrics help to track the performance of the security team and monitor the overall level of information security within the company or organization, measure the effectiveness of realized initiatives and manage compliance to standards, best practices and regulations.
Risk Assessment & Management
Risk management is one of the key processes for security information. Defensys SGRC allows calculating direct and indirect risks associated with information security by using one of the built-in methodologies including ISO 27005, NIST, OCTAVE, FAIR, basic 3-level schemes and Defensys proprietary methodology. Custom risk assessment methodologies are also supported.
Asset value implemented security controls and measures, and historical risk rates are taken into account while performing a risk assessment.
Risk Maps & Mitigation Plans
Defensys SGRC automatically generates a risk map indicating
- risk sources and factors,
- required security measures,
- related incidents,
- mitigation steps,
- historical risk level values.
Risk map data is automatically included in consecutive assessments.
The software also produces a risk mitigation plan with the estimated cost and effectiveness of the risk mitigation strategy chosen. It also allows us to keep track of the implemented measures and monitor the risk level changes over time.
Automated Audits & Compliance Checks
Information security audits are necessary to keep an eye on and control the state of information security in the organization. Defensys SGRC Platform helps to build a comprehensive compliance control system with regulatory and industry standards + supports proprietary security standards and checklists. Out-of-the-box users can work with the following frameworks:
- ISO 27001
- GDPR
- PCI DSS
- SWIFT CSP
- UAE IA Regulation
- SAMA Frameworks
- MAS TRM
- Shariah Governance Framework
- KSA NCA Essential Cybersecurity Controls
Upon the end of an audit, the software calculates an overall index of compliance and generates a report indicating the status of each requirement. This report helps in defining steps needed to improve compliance.
Mapping of Crossing Requirements
Some companies need to comply with several information security standards and this may require even more time and resources. Defensys SGRC Platform has a mapping of requirements feature which allows associating similar requirements of different standards and automatically track the related control measures which have been implemented.
The software automatically checks mapped requirements during an audit and completes relevant forms.
Checklists & Task Management
While performing an audit it is necessary to document problems and deficiencies. Once an audit is performed the software automatically generates a comprehensive checklist of problems that should be resolved.
- Automated assignment of responsible persons;
- Specification of deadlines;
- Indication of severity level and associated assets;
- Automated generation of tasks associated with problems;
- Easy tracking and control of the remediation status.
IT Infrastructure Control
A clear view of the IT environment is crucial for efficient information security management. Defensys SGRC Platform provides a comprehensive insight into the company’s IT infrastructure by collecting data via built-in inventory tools and integrated security solutions. It allows to the identification of critical IT assets and assigning staff responsible for their security.
- Aggregate and display at one single console details of the IT infrastructure items and their security status
- Determine critical assets and systems
- Control the installed software
- Reveal unauthorized software
- Manage vulnerabilities
- Control user privileges control
Security Level & Measures Control
Defensys SGRC helps to control the company’s security level through automated data collection from available security tools and external information systems, and enables:
- Centralized storage of all information security documents and data;
- A comprehensive description of each document with the specification of validity, persons responsible for review and update, list of users with access rights, and other details;
- Tracking of implemented security measures;
- Specification of responsible persons, financial data and other details for each measured item;
- Counting the amount and status of the implemented security measures while calculating the risks with automated updates.
Flexibility
Defensys SGRC supports custom databases of threats and security measures, proprietary value levels, scales, security properties and requirements. Risks can be calculated using custom risk assessment schemes and methodologies.
Users can create new document types with specific properties, upload proprietary documents, security standards and requirements, and apply customized mapping of crossing requirements.
Visualization & Reporting
Defensys SGRC brings visibility into security operations through
- Customizable dashboards, diagrams and charts;
- Graphical charts help to easily track the historical risk index changes, control statuses of risk mitigation measures and assess the effectiveness of the risk mitigation strategy;
- Audit charts which facilitate monitoring of the compliance level and its historical changes, and the status of unresolved problems;
- Built-in metrics for easy performance tracking;
- Automated reports generation using predefined templates or a custom report builder and scheduled delivery to recipients.
