Web Application Firewall (WAF)
We take your online security more seriously
Web Application Firewall (WAF)
KNOW MORE ABOUT Web Application Firewall
Keeping your Web applications safe, is one of the most challenging missions in information security because Web applications constantly change to meet business requirements, the security model must adapt as changes are made to the applications. Also, and because data centers are highly optimized, deploying an application security solution must require minimal changes to the existing infrastructure.
Web Applications
Web applications have became the backbone of business in nearly every part of the economy. They connect employees, customers, and partners to the information they need anywhere and anytime. This universal information accessibility has cut costs and dramatically accelerated the pace of business. Unfortunately, as the information accessibility has grown, so too has risks. Identity theft, data leakage, phishing, SQL injection, worms, application Denial of Service (DoS) attacks, and malicious robots increasingly target Web applications with consequences that impact companies.
Attacks Examples
SQL Injection attacks takes advantage of input validation vulnerabilities in custom Web application code to send unauthorized SQL commands to a back-end database. For example, using SQL injection, an attacker may gain access to the entire contents of a backed database including identity information. SQL injection is usually carried out by an external attacker from outside the perimeter firewall.
Cross–site Scripting attacks take advantage of script injection vulnerabilities in custom Web application code to redirect a customer’s login credentials to an attacker. Often used as part of a larger phishing scheme, cross-site scripting is usually carried out by an external attacker from outside the perimeter firewall.
Cross site Request Forgery attacks exploit a server’s trust in a client that presents a valid session token. The attacker abuses this trust by invoking an action on behalf of the victim through malicious code in a hyperlink, image source tag, script, i frame or other content.
Worm Infections take advantage of vulnerabilities in underlying operating systems and commercial software platforms. Code Red, Nimda, and MSBlaster represent just a few widely known worms targeting Web application platform software. In the case of identity theft, platform software vulnerabilities may be exploited by worms (or individual attackers) to install Trojan horse programs to enable back-door access to identify information.
The strengths and weaknesses of other security solutions
Network firewalls provide network layer access control and attack protection services. They have been uniformly deployed at the network perimeter and in front of critical internal enterprise resources – such as Web applications. As a component of overall Web application security architecture, network firewalls provide necessary protection against network-layer attacks. They also provide a barrier against the spread of worms from employee desktops to internal Web servers. While network firewalls prevent network-layer attacks and worm propagation, firewalls must allow all HTTP and HTTPS traffic to Web servers. Over time, the hacking community has learned to use this fact to their advantage by embedding attacks into Web traffic. Code Red and Nimda are examples of Web worms that easily traverse network firewalls via HTTP protocol-compliant communications.
Similarly, SQL injection and cross-site scripting represent two targeted Web application attacks (among many) that are ignored by network firewalls since they comply with network and HTTP protocols. As long as attacks are carried out via commonly allowed application protocols, network firewalls are ineffective.
The broader security industry has responded to the need for a deeper understanding of application layer behavior with intrusion prevention systems (IPS). IPSs look at the contents of a packet’s payload and compare it to a list of known attacks (signatures or other defenses) derived from documented vulnerabilities in commercial software. IPS technology may also enforce protocol restrictions to protect against known protocol related vulnerabilities in commercial software. Since virtually all worms are based on known software vulnerabilities, IPS can be an effective worm defense and therefore a useful component of a comprehensive Web application security architecture.
Unfortunately, IPSs are ineffective against targeted Web application attacks targeting unknown vulnerabilities in custom code. Since the vulnerabilities are unknown, no signatures are available.
Monitoring only (“sniffer”) products do not ensure complete protection from Web application attacks. Because they are deployed out of line, these products may not block every attack that has been detected. Usually, these products use a TCP reset for blocking attacks. In some cases, the latency involved in sending the reset after the attack is detected allows certain attacks to reach the victim. Hence, monitoring only solutions can only provide “best effort” protection for Web applications.
Web Application Vulnerability (AV) Scanners are tools used to automatically scan Web applications for potential vulnerabilities. Unfortunately, many vulnerabilities are only discovered during production run-time. Often, the application developers and the IT department are at odds, because while these vulnerability scanning tools enable visibility into application vulnerabilities, they do not alleviate or help reduce the time to production.
Typically, there are multiple cycles of scanning, code fixes and testing with unscheduled “rush” fixes that are costly and potentially disruptive.
While code review is a good idea, and is consistent with coding best practices, code review projects can entail significant ongoing personnel costs, lost of application deployment flexibility and resource allocation issues.
In addition, considering that applications change frequently, there may be multiple code review and code fix-testing cycles for every application product release and this often implies the need for emergency fix and test cycles. Furthermore, if an organization is using third-party or legacy applications, the source code often will not be easily available or easily understood which makes the likelihood of quickly fixing the discovered vulnerabilities very low.
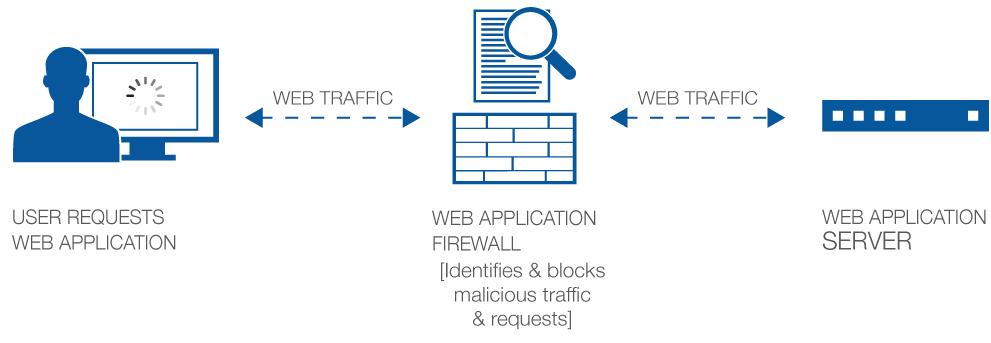
What is a Web Application Firewall
A Web Application Firewall is an enhanced firewall appliance that operate on data at layer 7 of the OSI reference model and protect Web servers and Web based Applications from attacks.
WAF acts on browser and HTTP attacks that try to manipulate application behavior for malicious purposes, and look for violations in application-specific policy.
Typically WAF enforce security policies at a very granular level by:
1- Building a model of the manner in which users interact with the application
2- Preventing traffic that does not adhere to that model. This model is called the positive security model.
The user benefits can be quantified as:
- Compliance– Advanced, built-in security protection and remote auditing helps organizations comply with industry security standards, including PCI DSS, HIPAA, Basel II, and SOX, in a cost-effective way—without requiring multiple appliances, application changes, or rewrites. Detailed PCI reporting determines if PCI DSS compliance is being met and provides steps required to become compliant if not.
- Security – patching against web application vulnerabilities to protect from a broad spectrum of threats, including the latest (D)DoS, brute force, and SQL injection attacks as well as cross-site request forgery. This advanced application-layer gateway stops hackers and attacks and ensures legitimate users can access applications, and furthermore, only legitimate requests are allowed.
- Out of the box protection – by using a set of pre-defined application policies, the rapid deployment features, the WAF can offer security for various applications with minimum configuration time.
- Agility – in conjunction with Web Applications Scanning solutions, the WAF can automatically build security policies for the vulnerabilities discovered by the web applications scanners.
The WAF is usually deployed inline, just in front of the web applications. Some WAF devices can be deployed also off path, for monitoring purposes.
In order to be effective against threats, the WAF solutions are to be deployed inline in protect mode – then several considerations are to taken into account:
- Usually the WAF is deployed in transparent mode, with no IP addressing on the traffic interfaces. Thus, the WAF should have fail-open functionalities – if the WAF becomes unusable, the user traffic should pass through.
- Minimum latency – the latency induced in the network by the appliance has to be minimum – milliseconds would be advisable
- The enforcement of the security policies is to be done in stages – first deployed non-intrusively, and upon successful testing only the security policies are to be enforced in place.
- Proper performance dimensioning in order to withstand peak traffic, in terms of both legitimate and malicious traffic; if the device cannot operate properly under heavy load this will result in huge business impact
- Access policies have to be reviewed each time a modification has to be operated to the application, at both the application and at user access policies; failing to do this can result in blocking legitimate traffic and/or blocking legitimate users’ access.
- User access audit can consume very severely the resources.
